Packet traces are collected whenever packets match a security rule. The packet trace can be downloaded, or decoded.
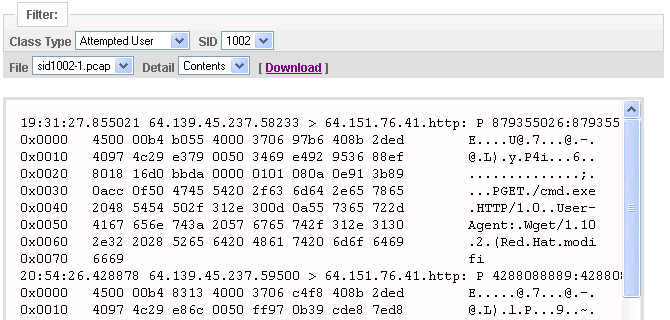
The packet trace confirms that the packets match the rule and is an accepted way of documenting a security problem.
This concludes the final example in the product walkthrough. Further information is available from the InMon Corp. web site at www.inmon.com.