Controlling Traffic
Typically, a small number of hosts are responsible for the majority of traffic on the network: identifying those hosts and applying controls to their traffic prevents them from unfairly dominating, ensuring fair access to all users.
Peer-to-peer protocols (P2P) pose some unique challenges:
- P2P protocols make use of very large numbers of connections in order to quickly transfer data. The large number of connections allows a P2P user to obtain a disproportionate amount of network bandwidth; even a small number of P2P users (less than 0.5% of users) can consume over 90% of the network bandwidth.
- P2P protocols (and users) are very good at getting through access control lists (acl) by using non-standard ports, using port 80 (web) etc. Trying to maintain an effective filter to identify P2P traffic is a challenge and the resulting complex rule sets consume significant resources in devices attempting to perform classification.
The following diagram shows the elements of Traffic Sentinel's traffic control function:
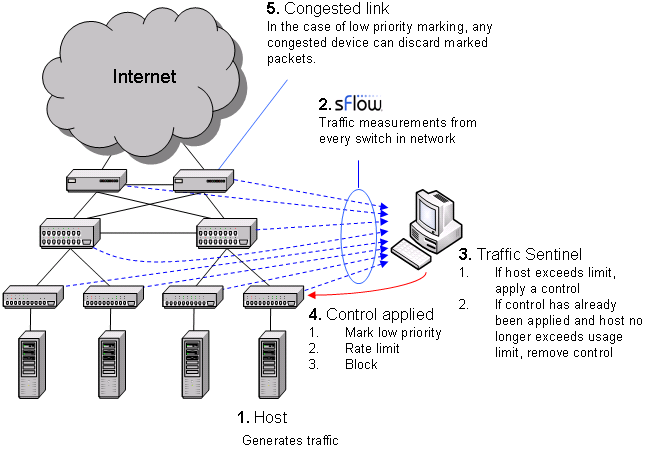
The diagram shows the sequence of actions involved in controlling traffic. The sequence form a "closed-loop control system" designed to maintain network performance by controlling large sources of traffic. In step 1, a host starts generating large amounts of traffic. In step 2, Traffic Sentinel, using the multi-vendor sFlow® standard to continuously monitor traffic throughout the network, quickly detects the increase in traffic from the host and locates the host to the switch port connecting it to the network. In step 3, Traffic Sentinel checks the host's traffic levels against pre-set limits (or quotas) and applies a control if the host is over quota. In step 4, the access switch connecting the host to the network is reconfigured to apply the selected control. Step 5 only applies when using priority controls. A priority control consists of two parts; the first part involves marking packets from the host as low priority at the access switch and the second part occurs when congestion occurs elsewhere in the network and the congested device selectively drops the marked packets, reducing the bandwidth consumed by the marked host. Finally, Traffic Sentinel continues to monitor traffic and when it detects that the traffic from a host is back within acceptable limits, it removes the control.
In this example, we will be setting usage quotas in order to manage P2P traffic on a University campus.